We live in a world where software is the critical component of almost everyone’s life. The software creates a connection to almost everything. So, whether you are in your car, at home, or at your workplace, you will have to use the software in one way or another. To function optimally, the software will have to run huge lines of code.
If you are a software developer, then you are well conversant with what code signing certificate is and what it entails. Each developer needs a cheap code signing certificate that offers dual benefit like cost efficient and code integrity with strong encryption. You can find it from different SSL providers including direct certificate authorities.
Besides its availability, we first need to discuss about what a code signing certificate is, what code signing entails, and finish by looking at a comprehensive guide on some of the best code signing certificate practices.
What is a Code Signing Certificate?
So, what is a code signing certificate? Code signing refers to all the procedures and tools needed to sign your code by a trusted Certificate Authority. For the Certificate Authority to sign a code, it will first have to validate the identity of the certificate author who submits the software. The author validation process is primarily meant to assure users that the software owner is genuine and legitimate.
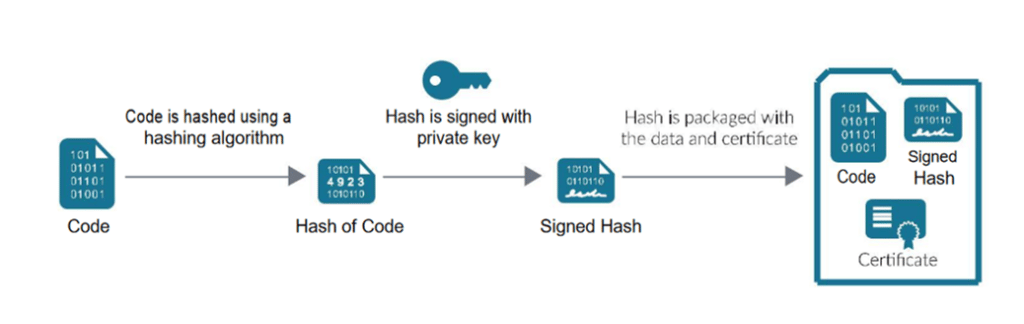
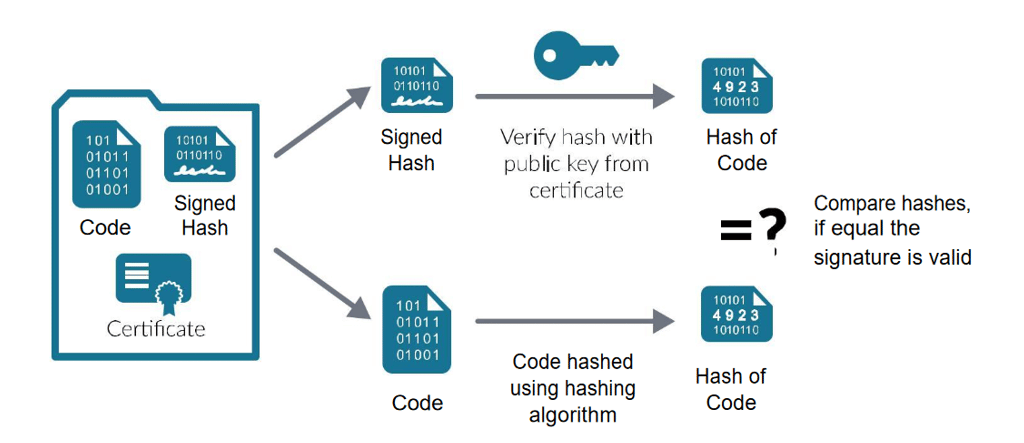
Once the Certificate Authority has authenticated the validity of a code, the Certificate Authority will issue a code signing certificate. The code signing certificate carries all the key details about the organization’s identity that owns the software. The certificate will bind the entity’s identity to a public key which is usually mathematically related to a private key pair. In essence, the developer will use a private key to sign a code, whereas the end-users will use the developer’s public key to establish the developer’s identity.
A code signing certificate, therefore, plays a very vital role in software and code security. If you are a software developer, you have no option but to get a code signing certificate.
Code Signing Certificate Best Practices
Although code signing helps with security issues, lousy code signing certificate practices can make your certificate vulnerable to attacks. In the past, we have seen cases where codes have been compromised, leading to the spread of malware and other devastating impacts.
The ASUS APT attack is one perfect example where hackers exploited a vulnerable code, planted and executed a malware attack. The SolarWinds Cyber-Attack is another example of how attackers exploited software to insert a backdoor and trojan horse installation packages. Attackers were able to exploit the code to gain unauthorized access into the SolarWinds systems.
Such code-exploitation cases continue to rampage the streets. The effectiveness of a code signing certificate as a software authentication strategy depends upon the secure handling of the code by the owners and developers. Software authors and developers should be diligent and willing to invest in proper code signing certificate best practices. In doing so, they will be making the possible compromise of the code signing certificates highly unlikely.
You should put several code signing best practices into action to ensure that all your codes are adequately secured. The National Institute of Science and Technology (NIST) has recommended several measures that you should adhere to ensure that your codes are safe.
The following are the code signing best practices that you should know about.
Implement Strong Key Security
A signing key is the most essential yet delicate part of your code signing certificate. An exfiltrated, lost or compromised key could be the starting point of a major cyber breach. The signing key is the most sought component of your code signing certificate by hackers. They are lucrative as they can be sold on the dark web. And it will be interesting to note that their pricing on the dark web is higher than that of drugs, passports, and guns.
You do not wish to lose your private key to malicious people who want to sell it on the dark web or use it for other malicious purposes. As such, you must ensure that you do all you can to safeguard your private key from malicious actors.
Here are some tips to safeguard your private key:
- Limit access to only authorized people.
- Have adequate physical security controls to limit access to private keys.
- Limit the number of computers that can access your code.
Ensure that you Time Stamp the Code
A timestamp refers to a small data piece that is usually included in a certificate signature. Timestamping helps to extend the trust of a certificate beyond its validity period. In essence, timestamping helps verify a code signing certificate even after the code has expired.
Usually, a user would have to go through extra procedures to make a call to the timestamp servers. However, it is essential to note that these procedures are necessary, and they are for the good and safety of your code signing certificate. Failing to timestamp your certificate will render the certificate invalid after the expiry period.
Timestamping has been seen as the best code signing certificate because it helps with code verification even after the expiry or revocation of a code signing certificate.
Implement Cryptographic Hardware Solutions to Safeguard Private Keys
Another critical practice that you should adopt to protect your code signing certificate from security vulnerabilities is to use cryptographic hardware solutions to secure your private keys.
For instance, it is highly recommended that you use Federal Information Processing Standard (FIPS) 140-2 Level 2 certified cryptographic products. The good thing about using such products is that they do not allow private keys export.
While using cryptographic hardware solutions, you must remember to physically secure the devices safely to protect them from possible thefts.
All the hardware devices carrying private keys should be protected from using strong and unique passwords that hackers cannot easily break through.
Finally, all dormant keys should be destroyed, either by overwriting them or physical destruction. This is one of the most fundamental recommendations of the Microsoft code signing best practices.
Understand the Difference between Release-Signing and Test-Signing
It is always essential to know which certificate signing you are working with and always keep them separate. With Test-signing, you do not have to go through many demanding security standards and procedures, as is usually the case with development code signing certificates. Most times, the test signing certificates are usually self-assigned.
Release signing certificates are essentially applied in signing production codes which are then shipped to the end-users. Therefore, release signing certificates are usually trusted on a global scale.
It would be best to craft an entirely separate code signing infrastructure for Test signing and Release signing processes as a best practice. Most importantly, keep in mind that test signing private keys require less rigorous security access controls and procedures, unlike release signing certificates.
Frequently Scan the Codes Before Signing
You must fully understand the role of a code signing certificate. Please note that a code signing certificate is not responsible whatsoever for upholding the safety or quality of your software, executables, or scripts. The code confirms the legitimacy of the publisher or author by checking whether the code has been tampered with in any way since it was published.
If your certificate is used to sign an infected software or code, you are liable to all the repercussions. Your code is most likely to be revoked if that is the case.
So, before signing the code, it is prudent to ensure that you perform a full code scan to eradicate vulnerabilities that could cause unforeseen bugs and malicious snippets. In addition, running virus scans will help to improve the security of the released codes.
Always Authenticate the Code Before Signing
You have to be sure that your software, scripts, and executables are set to be signed. It would be best if you documented all the code signing all signatures by developing a full approval. Doing this is necessary for compliance purposes and incident response. This is a best practice that should be employed in the actual code development stage.
The following are the best practices that you must follow for authenticating a code:
- Before signing and officially releasing the software, scripts, executables, or files, ensure that they are all fully authenticated.
- Have a separate process for your code signing submissions and approvals to avoid falling into the trap of malicious, defective, and unapproved codes.
- Ensure you document all code signing activities for auditing and incident response.
Avoid Overusing one Private Key (Diversify the Risk)
There is always an attached degree of risk every time you use your certificate. Although the mathematics applied in modern-day computers can make it hard for hackers to crack a code, there is always a risk involved. Messing up with your key to the extent of it being revoked might invalidate other signatures and good codes.
If you have heard of the saying “do not put all eggs in one basket,” then you know how dangerous it can be to use a single code. As a best practice, always diversify your risk by using multiple codes.
Revoke Compromised Code Signing Certificates
Sometimes, things might not go so well with your code signing certificate, requiring that the code be revoked. Unless in the case where you have timestamped your certificate, code revocation will lead to certificate invalidation. To avoid the repercussions that come with an invalidated certificate, you should inform your Certificate Authority about issues that can compromise your code.
Have a Centralized Code Management Strategy?
The modern IT infrastructure and organization’s nature have made it difficult for organizations to have centralized management of code management strategies, tools, processes, and infrastructure. Although this is the case, it remains vital that organizations have a central code management system. This reduces the risks associated with having a decentralized code management system.
Conclusion
Software developers often take code security for granted until they fall victim to a devastating security breach. However, you do not have to sit and wait. It would be best if you rose to the occasion as early as possible to avoid regrets. Get a code signing certificate, and follow the best practices talked about in this article.
